
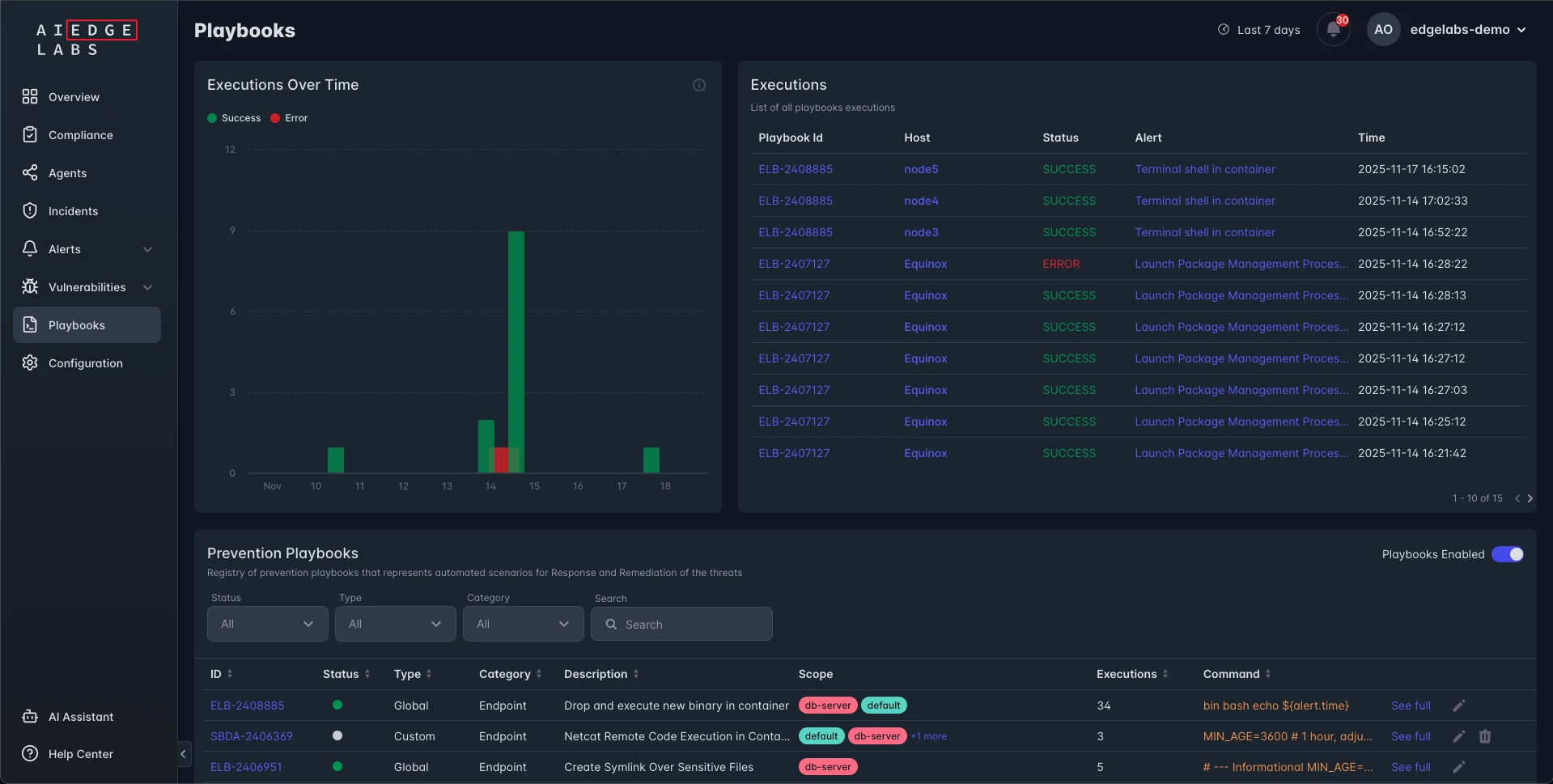
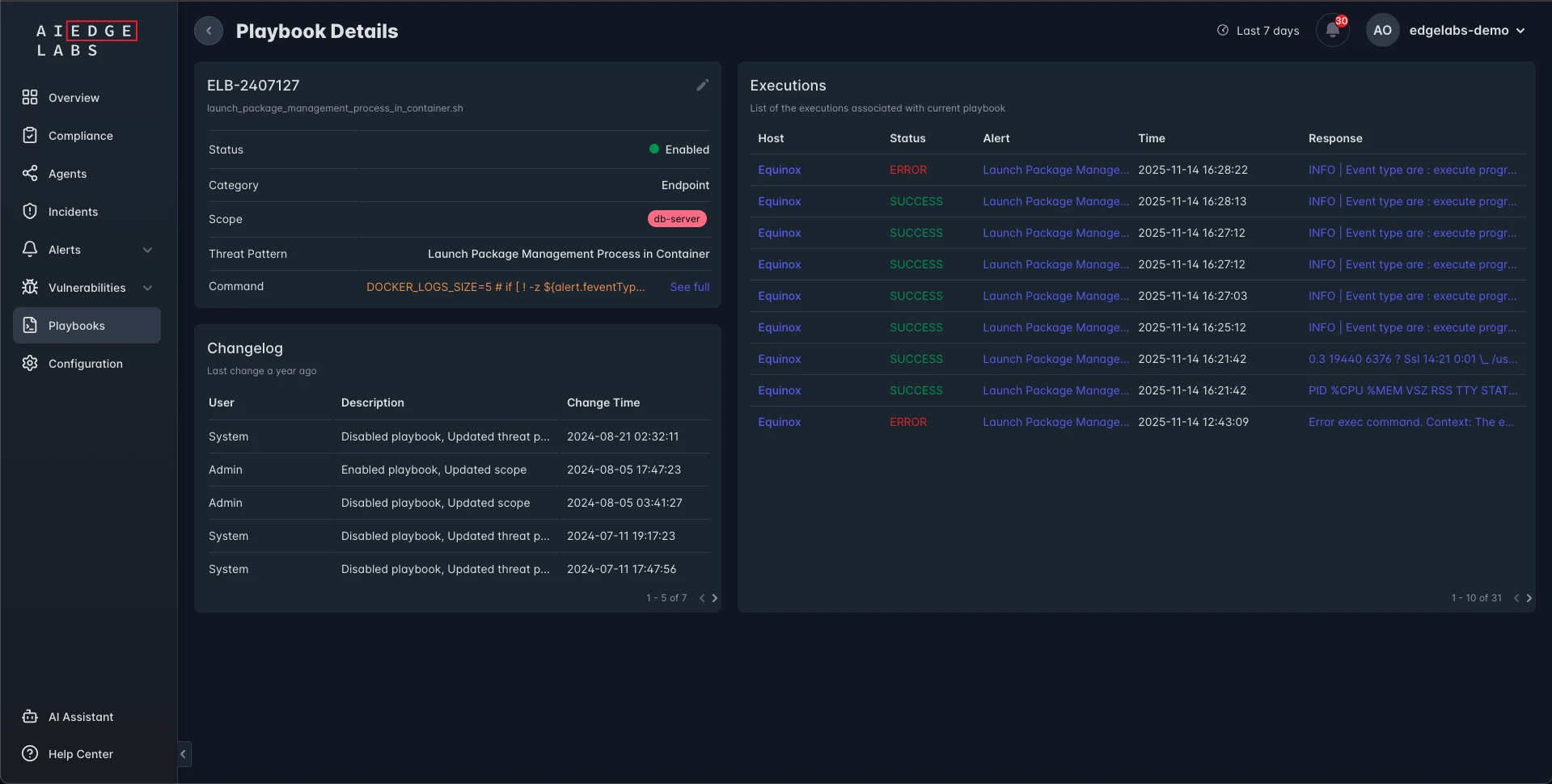
AI-Generated Playbooks
Transform your response: innovative automation for runtime alerts
Reimagine Threat Mitigation with AI-Generated Playbooks
AI-generated playbooks revolutionize the way SOCs handle alerts. Powered by cutting-edge LLMs, playbooks
deliver real-time, customized responses tailored to each incident, boosting efficiency and accuracy in
threat mitigation.
Harness the Future with LLM Models
Say goodbye to manual alert analysis! Our revolutionary LLM models dive deep into complex runtime data,
extracting critical details and crafting bespoke response strategies in real-time.
Insightful Investigations, Actionable Plans
Our AI-generated playbooks are a two-pronged powerhouse: the Information Playbook and the Action Playbook.
Information Playbook
Action Playbook
Information Playbook
Illuminate threats with investigative insights that help your SOC understand and neutralize
attacks.
Process Inspection
Review suspicious process histories and behaviors.
File Analysis
Track file modifications and access for malicious activity.
Network Investigation
Map and cut off malicious connections.
Log Review
Trace activity through system and application logs.
Action Playbook
Respond with precision. The Action Playbook provides clear, automated steps to neutralize
threats and restore security — fast and reliably.
Process Termination
End rogue processes instantly with targeted commands, stopping malicious activity in its
tracks.
Network Blocking
Isolate threats by blocking malicious IPs or ports, cutting off unauthorized
communication.
Execution Disabling
Prevent harmful binaries and processes from running again, ensuring persistent threats
are eradicated.
System Updates
Reinforce security posture with guided system update recommendations, closing known
vulnerabilities and preventing repeat exploitation.
Do You Want to Improve Your SOC?
Execute with Confidence. See Immediate Impact.
Our playbooks include ready-to-use commands and scripts for SOC teams, enabling rapid execution and fast
results.
Seamless Adaptability for Any Environment
AI-generated playbooks are designed for maximum flexibility:
Edge Nodes & On-Prem Servers
Deploy directly with AI EdgeLabs agents via VPN or SSH.
Cloud Systems
Manage and execute centrally with robust cloud integrations.
Kubernetes Clusters
Scale seamlessly across nodes using Helm charts.
IoT Gateways
Lightweight deployment optimized for edge-specific scenarios.
Ready to Transform Your Security Operations?
Step into the future with AI-generated playbooks and unleash the full potential of your SOC. Act now and
stay ahead of evolving threats — your security evolution starts here.



